Hello team,
I’ve been going through this TLS guide with the option of the pre-existing certificate.
For some devices, it shows a secure site however I can’t log in both as an admin or an offline user. For some, it redirects back to the unsecured version, and can easily log in.
Could you please point me to some additional information I need to apply to fix this?
Thank you.
1 Like
Hi @Japheth_Kiprotich!
We can help sort out your SSL issues. A few questions, so we can gather more information about your setup:
Hello @hareet,
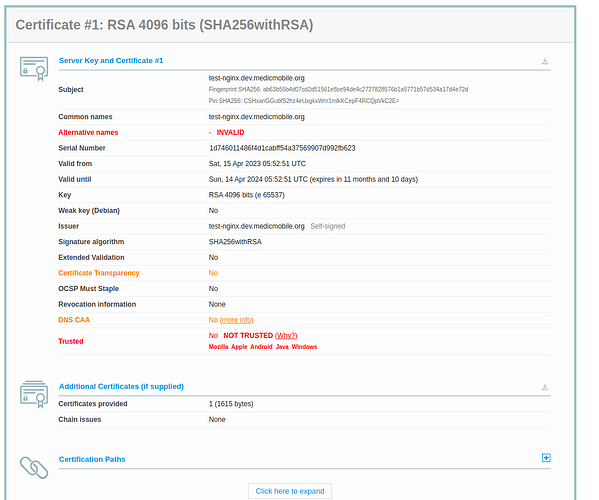
Attached is the screenshot of the output
For the mobile device, I have tested with Android 11 but mostly I have been trying out using my computer’s browsers Mozilla and Google Chrome
@Japheth_Kiprotich Thanks for sharing the output of that SSL Labs test!
Unfortunately, you won’t be able to generate a valid SSL certificate for someone else’s domain. For example, you need to create an SSL Cert for a domain you own (i.e. japheth-kiprotich.com). During SSL cert generation (letsencrypt), you will have to verify you own that domain by pointing a DNS entry to your machine.
For production SSL deployment:
- Purchase a domain name (japheth-kiprotich.com)
- Add a DNS entry in your domain provider’s management interface that points the ip address of your CHT project
- Follow our TLS guide to run letsencrypt/certbot to generate SSL certs and place them into the nginx container
For development purposes, instead of purchasing a domain, you could try following this setup:
More information about that setup can be found in this Forum post: CHT Docker Helper Gets Fix to DNS issues with local-ip.co
1 Like
@hareet, I’m just curious how this should be. I have verified the certificate files with the above using default apache2 and I’m getting a successful validation
Hi @Japheth_Kiprotich !
I’m sorry to hear your issue persists  Let’s try and fix it!
Let’s try and fix it!
Let’s confirm you have the correct certificate files installed in the CHT’s nginx container. Please copy and paste all this code, exactly as it appears, and run it on the CHT server. Please post back the results:
echo;echo "--------COPY BELOW-----"
nginx=$(docker ps --filter "name=nginx" --format '{{ .Names }}')
echo "nginx container is: ${nginx}"
echo;echo "Cert Files in nginx:"
docker exec -it ${nginx} bash -c "ls /etc/nginx/private/"
echo;echo "Common Name and Issuer:"
docker exec -it ${nginx} bash -c "openssl x509 -noout -subject -issuer -in /etc/nginx/private/cert.pem"
echo;echo "MD5 of modulus, these two lines should match:"
docker exec -it ${nginx} bash -c "openssl rsa -modulus -noout -in /etc/nginx/private/key.pem | openssl md5"
docker exec -it ${nginx} bash -c "openssl x509 -modulus -noout -in /etc/nginx/private/cert.pem | openssl md5"
echo;echo "Full chain output::"
docker exec -it ${nginx} bash -c "openssl crl2pkcs7 -nocrl -certfile /etc/nginx/private/cert.pem | openssl pkcs7 -print_certs -noout |tr -s '\n\n'"
For example, this is what I get when I run it:
--------COPY BELOW-----
nginx container is: townhall_nginx_1
Cert Files in nginx:
cert.pem key.pem
Subject Name and Issuer:
subject=CN = *.local-ip.medicmobile.org
issuer=C = US, O = Let's Encrypt, CN = R3
MD5 of modules, these two lines should match:
(stdin)= 22a0fab284a590faa8a8f46d5584ce1f
(stdin)= 22a0fab284a590faa8a8f46d5584ce1f
Full chain output::
subject=CN = *.local-ip.medicmobile.org
issuer=C = US, O = Let's Encrypt, CN = R3
subject=C = US, O = Let's Encrypt, CN = R3
issuer=C = US, O = Internet Security Research Group, CN = ISRG Root X1
subject=C = US, O = Internet Security Research Group, CN = ISRG Root X1
issuer=O = Digital Signature Trust Co., CN = DST Root CA X3
Hey, @mrjones thank you for the suggestion.
Here is the output of the above code
--------COPY BELOW-----
nginx container is: app-devl_nginx_1
Cert Files in nginx:
cert.pem key.pem
Common Name and Issuer:
subject=CN = *.local-ip.medicmobile.org
issuer=C = US, O = Let's Encrypt, CN = R3
MD5 of modulus, these two lines should match:
(stdin)= 22a0fab284a590faa8a8f46d5584ce1f
(stdin)= 22a0fab284a590faa8a8f46d5584ce1f
Full chain output::
subject=CN = *.local-ip.medicmobile.org
issuer=C = US, O = Let's Encrypt, CN = R3
subject=C = US, O = Let's Encrypt, CN = R3
issuer=C = US, O = Internet Security Research Group, CN = ISRG Root X1
subject=C = US, O = Internet Security Research Group, CN = ISRG Root X1
issuer=O = Digital Signature Trust Co., CN = DST Root CA X3
@Japheth_Kiprotich - thanks for the update!
Your response confirms you have the insecure certificate Medic publishes here. This should only be used for development as the private key has been intentionally published.
If you would like to use the insecure certificate already installed, you can use the IP address in the URL to visit it. So if the server’s IP is 214.53.35.53, you would use the URL https://214-53-35-53.local-ip.medicmobile.org
If you would like to install your own certificate for your own domain, you need to:
- Ensure the DNS for your domain resolves to the static, public IP of your server. For example, if your IP was
214.53.35.53 and your domain is cht.example.com then you would update your DNS so that cht.example.com resolves to 214.53.35.53
- Download the full chain into the
cert.pem file and the private key into the key.pem from the certificate authority
- Copy these two files to the CHT server
- Follow the steps to copy TLS certs into a CHT server.
Alternately, that same page has instructions for using Certbot to get free certificates. Note that these Certbot instructions require CHT 4.2.0 or later.